|
We'd like to introduce you to IdentiPHY! Check out our one-pager below... IdentiPHY enables true multi-factor device authentication on your network. Two-factor authentication is commonplace these days with username/password, tokens, text messages, and even biometrics being used to authenticate users. However, the same level of authentication is not being applied to devices.
The three pillars of authentication:
For devices, "Something you have" and "Something you know" are the same thing! So, what is the equivalent of "Something you are" for devices? Enter IdentiPHY! Reach out to learn more or setup a demonstration of IdentiPHY within your network.
0 Comments
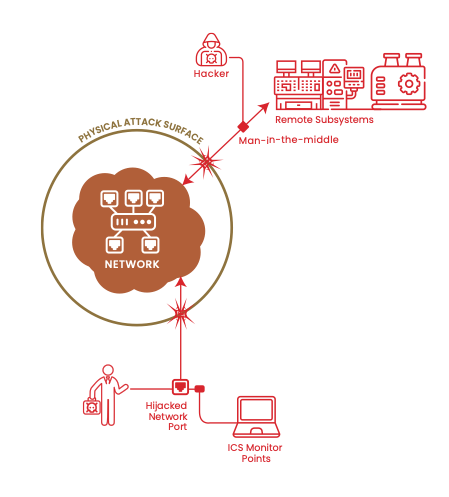 In a recent blog posting, Dark Wolf Solutions described some of their techniques for performing penetration testing and a particular assessment job that they executed. The main goal of this job was gaining physical access (which they quickly did) and installing a rogue wireless access point (AP) to the client's production network running Dynamic Host Configuration Protocol (DHCP). “We configured … our rogue access point (that we would ultimately attempt to plug into their DHCP enabled production network via a vacant and active network jack and/or by changing the MAC (Media Access Control) address on the rogue AP to match something like a VoIP (Voice Over IP), just in case there was any sort of MAC filtering).” These techniques are commonly employed to gain access to a target's network. In some instances, an attacker will even leave behind a small device (think RaspberryPi) to gain remote network access via the local cellular network. Now they can leave your facility and begin moving laterally throughout your network with relative impunity. Your network's physical attack surface is present in every office, cubicle, conference room, and lab throughout your facilities. For a wired network, the vulnerable points of attack are the network jacks fixed to wall plates and cube walls. If the first (logical) line of defense for these network jacks is MAC address filtering then your network is vulnerable to attack. MAC address filtering is a basic Layer 2 protection that should be deployed throughout your network. It limits the hardware devices that can be used on a particular switch port and is provided by most manufacturers of managed switches. This capability is often called Port Security or "Sticky MACs". However, MAC spoofing is a "script kiddie" level of attack these days. 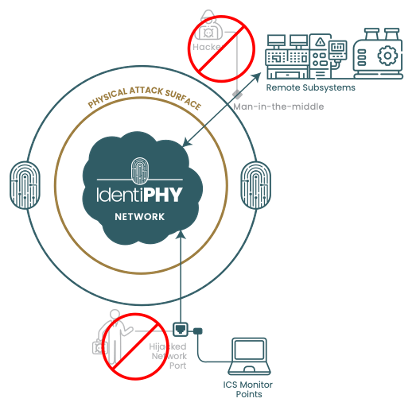 The IdentiPHY:Wired platform adds a novel logical ring of protection around your network's most vulnerable ports. It protects your network from physical layer attacks 24 hours a days, seven days a week by authenticating the devices connected to your network. In most instances, the presence of an unauthorized device can be detected before it can even be issued an IP address from your DHCP server. Reach out to learn more or see a demonstration of IdentiPHY within your network! |
ArchivesCategories |


 RSS Feed
RSS Feed